Which Type of Cryptography Uses Two Cryptographic Keys
Vernam key - Type of key invented by Gilbert Vernam in 1918. Admin Staff asked 2 years ago.
Public Key Cryptography Explained Sectigo Official
Asymmetric Key Cryptography Image Source Asymmetric Key Cryptography is completely different and a more secure approach than symmetric key cryptography.
. This is the original data message that the algorithm uses as input. What are the two types of forks. Choose the correct option from below list 1asymmetric 2secure 3private 4dual key cryptography Answer-1asymmetric.
Asymmetric Asymmetric What is the block cipher algorithm that operates on 64-bit blocks and can have a key length from 32 to 448 bits known as. Both parties must use the same cryptographic algorithm. A public key is used for encryption and a private key is used for decryption.
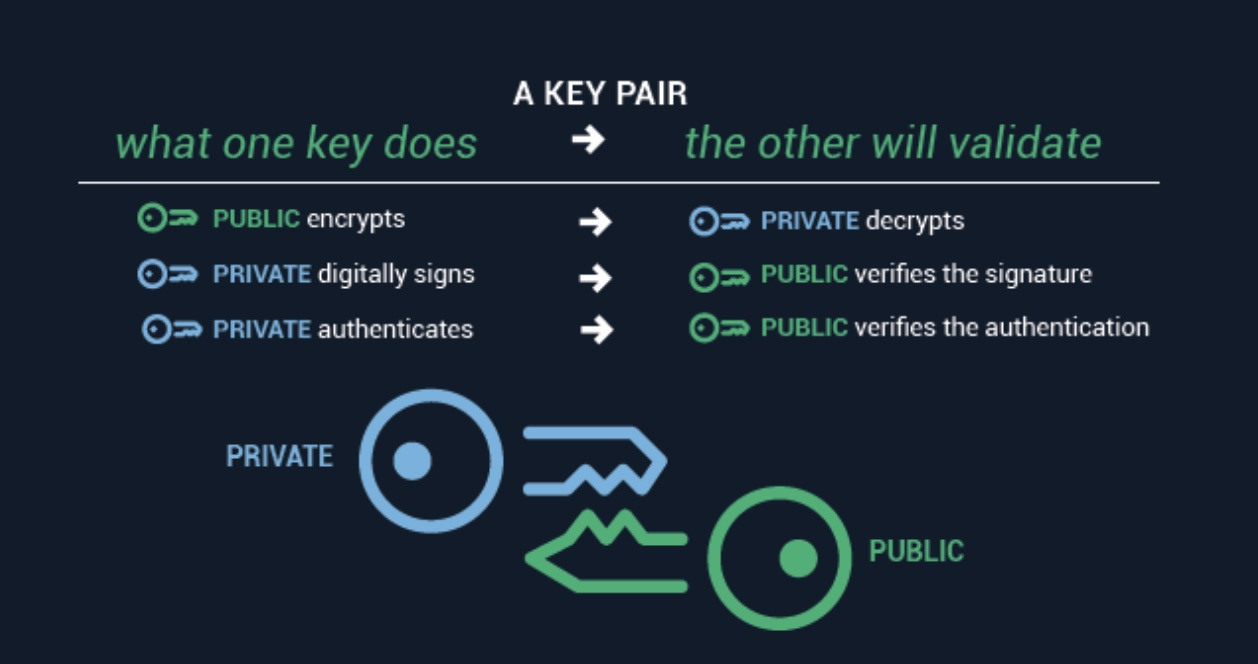
Asymmetric or publicprivate encryption uses a pair of keys. One is a public key whereas the other is called a private key. It is also called Secret-Key Cryptography.
One is used for encryption while the other key is used for decryption. Asymmetric Cryptography also popular as public key cryptography uses two keys to encrypt data. The following are smart contract programming languages except _____.
Protect the public key. Symmetric key encryption algorithms use a single symmetric key for both encryption and decryption whereas asymmetric key encryption algorithms aka public key algorithms use two different but related keys for encryption and decryption. 0 Vote Up Vote Down.
Select 2 answers 1. Which type of cryptography uses only private keys. What are the main tokens used as digital currency in Ethereum.
Which of the following is not one of the functions of a digital signature. Asymmetric Key Pair A matching publicprivate key pair whereby anyone can encrypt with the public key but only those who hold the private key can decrypt. Which type of cryptographic algorithm takes an input string of any length and returns a string of any requested variable length.
What type of cryptography uses two keys instead of just one generating both a private and a public key. To have intelligent cryptographic communications between two parties who are using a conventional algorithm this criteria must be satisfied. Which type of cryptography uses two cryptographic keys.
Asymmetric Key Cryptography. This encryption method uses a pair of keys an encryption key and a decryption key named public key and private key respectively. The key pair generated by this.
Another term for secret key cryptography is symmetric cryptography. The following are common types of cryptographic key. Public Key Cryptography This type of cryptography technique involves two key crypto system in which a secure communication can take place between receiver and sender over insecure communication channel.
What are the two types of accounts in ethereum. The cryptographic key that the sending party uses to encipher the data must be. Which type of cryptography uses two cryptographic keys.
See Type 2 product. The public key is known to anyone who wants to send a secret message to protect it from unauthorized access. Type 2 key - NSA keys used to protect sensitive but unclassified SBU information.
Asymmetric or public-key encryption is a type of cryptography that uses a pair of related keys to encrypt the data. A type of encryption scheme that uses a paired public and private key is known as. What type of cryptography uses two keys instead of just one generating both a private and a public key.
Under this system a pair of keys is used to encrypt and decrypt information. Type 1 key - NSA keys used to protect classified information. See Type 1 product.
The key pair generated by this algorithm consists of a private key and a unique public key that is generated using the same algorithm. IBM Security Key Lifecycle Manager uses both symmetric and asymmetric keys. Public key and Private Key are different.
The encryption algorithm performs various mathematical operations on this plaintext data to encrypt it. Zeroized key - key that has been erased see zeroisation See also. There are 5 components in a symmetric key algorithm.
Since a pair of keys is applied here so this technique is also known as asymmetric encryption. This is comparatively harder to use as the data can only be unlocked by using 2 different. When an asymmetric key pair is generated the public key is typically used to encrypt and the private key is typically used to decrypt.
Public The public key in a asymmetric key pair. Even if the public key is known by everyone the intended receiver can only decode it because he alone knows the private key. In this system every user uses two keys or a pair of keys private key and public key for encryption and decryption process.
On the other hand asymmetric key cryptography refers to an encryption technique wherein two different keys are used to encrypt and decrypt the data. Unlike private key cryptography if one key is used to encrypt that same. Asymmetric-Key Cryptography- This encryption method uses a pair of keys an encryption key and a decryption key named public key and private key respectively.
Private Private keys may be part of a publicprivate asymmetric key pair. Sender uses first key public key to encrypt the message and receiver uses second key private key to decrypt the message. The most renowned symmetric key cryptography system is Data Encryption System DES.
Data encrypted using one key can only be decrypted by using the other key in the publicprivate key pair.

What Is A Cryptographic Key Keys And Ssl Encryption Cloudflare


Comments
Post a Comment